1. What Is a Security Operations Center and Why Does It Matter?
What is a Security Operations Center?

The Role of SOC in Protecting Business Assets
Why SOC Is Essential for Security Monitoring and Incident Response
- 24/7 Monitoring: Threats don’t follow business hours, and neither does your SOC. A dedicated team ensures constant surveillance of your digital infrastructure.
- Faster Response Times: The ability to react quickly to security incidents can mean the difference between a minor disruption and a major breach.
- Holistic Visibility: SOCs provide centralized insights into your entire IT ecosystem, helping you detect not just external threats but also insider risks and misconfigurations.
- Regulatory Compliance: Many security standards (such as ISO 27001, GDPR, and PCI DSS) require continuous monitoring and documented incident handling, both of which a SOC provides.
- Business Continuity: By minimizing the impact of attacks, a SOC helps protect not only your systems and data but also your brand reputation and customer trust.
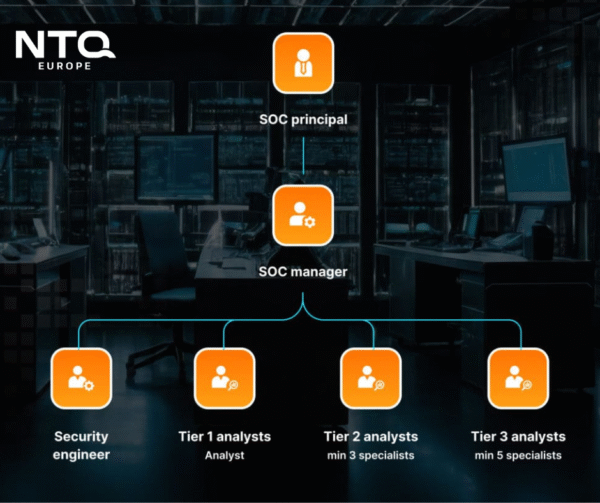
Structure of a typical SOC
2. What Happens When You Don’t Have a Security Operations Center
Trying to manage cybersecurity without a Security Operations Center is like trying to guard a fortress without watchtowers. In an environment where cyberattacks are faster, smarter, and more frequent, not having a SOC leaves organizations exposed. Below are three critical challenges that businesses commonly face without centralized security monitoring and why they matter.
| Challenge | What It Means for Your Business | Why It Matters |
| Lack of Centralized Security Monitoring | – Delayed Threat Detection: Without continuous monitoring, threats may go unnoticed until significant damage has occurred. – Inefficient Incident Response: Lack of a coordinated response plan can lead to prolonged recovery times and increased costs. – Compliance Violations: Inadequate monitoring and reporting can result in non-compliance with industry regulations, leading to fines and reputational damage. |
This fragmented approach increases the chance of missing early warning signs, allowing attackers to operate unnoticed until it’s too late. |
| More Frequent and Sophisticated Cyber Threats | As hackers become more advanced, threats like ransomware, phishing, and zero-day exploits grow harder to detect and stop. | Without a dedicated team and tools in place, your business may not have the resources or expertise to respond quickly, putting critical data and operations at risk. |
| Delayed Detection and Incident Response | – Alert Fatigue: Overwhelmed by numerous security alerts, teams may miss critical warnings. – Resource Constraints: Limited personnel and tools hinder effective threat detection and response. – Lack of Expertise: Insufficient cybersecurity knowledge impedes the ability to identify and mitigate threats effectively. |
The longer an attacker is inside your system, the more damage they can do. Delayed responses often lead to higher recovery costs, regulatory penalties, and loss of customer trust. |
A well-run SOC gives you the visibility, speed, and coordination needed to respond confidently when threats strike and, more importantly, to stop them before they do.
3. Key Components of an Effective Security Operations Center
An effective Security Operations Center is a carefully designed ecosystem of people, processes, and technologies working in harmony to keep your organization safe day and night. To truly protect your business from modern threats, your SOC must be built on three core pillars: layered security architecture, threat detection and analysis technologies, and a robust incident response process.
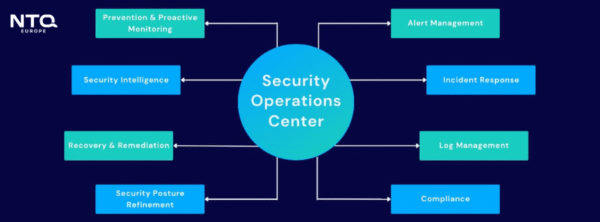
A SOC is built on three core pillars: layered security architecture, threat detection and analysis technologies, and a robust incident response process.
Multi-Layered Security Architecture
The foundation of any effective SOC is a defense-in-depth strategy. This means building multiple layers of security controls across every part of your IT environment, from endpoints and networks to cloud services and applications. Here’s how these layers work together:
- Perimeter Layer: Firewalls and intrusion prevention systems (IPS) defend the network’s outer edge by blocking unauthorized access attempts and known threats.
- Network Layer: Traffic is continuously monitored for suspicious behavior, lateral movement, or anomalies that may suggest an internal compromise.
- Endpoint Layer: Tools like Endpoint Detection and Response (EDR) secure laptops, workstations, and mobile devices, often the first target in cyberattacks.
- Application & Data Layer: Web application firewalls (WAF), database activity monitoring, and encryption protect sensitive business systems and customer data.
- Identity & Access Management: Ensures only the right people have access to the right resources, and only when they need it.
With layered protection, if one control fails, others are still in place to catch the threat. This structure makes your environment more resilient and significantly reduces the risk of a successful breach.
Threat Detection and Analysis Technologies
Modern threats are fast, stealthy, and often automated. To counter them, SOCs must rely on advanced, integrated technologies that provide real-time visibility across the organization. Key technologies include:
- SIEM (Security Information and Event Management): Collects and correlates security data from various sources (logs, endpoints, servers, firewalls), then uses rules and analytics to flag anomalies.
- Threat Intelligence Platforms: Feed your SOC with up-to-date information on malware signatures, known bad IPs, zero-day vulnerabilities, and emerging threats across the globe.
- User and Entity Behavior Analytics (UEBA): Uses machine learning to detect suspicious patterns like an employee logging in at 3 AM from another country or downloading abnormally large files.
- SOAR (Security Orchestration, Automation, and Response): Automates repetitive investigation tasks and coordinates incident response actions to accelerate time-to-resolution.
These technologies help your team detect threats before they cause damage and reduce the time and effort required to investigate and respond.
Incident Response and Remediation Process
Even the most secure systems aren’t immune to attacks. That’s why a well-practiced and well-documented incident response process is non-negotiable in any SOC. A mature SOC follows this 6-step response cycle:
- Preparation: Develop playbooks, assign roles, and train staff to ensure everyone knows what to do when an incident hits.
- Identification: Analyze alerts and telemetry to verify whether a security event is real and how serious it is.
- Containment: Limit the damage by isolating affected systems and accounts quickly, without disrupting the rest of the business.
- Eradication: Remove malware, backdoors, and any remnants of the attack from your environment.
- Recovery: Restore services, monitor for reinfection, and resume normal operations.
- Post-Incident Review: Learn from the event by analyzing root causes, updating policies, and refining detection rules.
Having a clear and fast response plan significantly reduces the impact of breaches, limits downtime, protects brand reputation, and builds internal confidence that your team is in control.

A well-implemented SOC will help transform the way your business responds to threats, protects sensitive information, and ensures operational continuity.
4. Benefits of Implementing a Security Operations Center
In an age where digital operations drive business success, more organizations are turning to a global Security Operations Center as the core of their cybersecurity strategy to protect their data and systems. A well-implemented SOC will help transform the way your business responds to threats, protects sensitive information, and ensures operational continuity.
Strengthened Protection of Business Data and Systems
Your data is one of your most valuable assets and also one of the most targeted. From financial records and customer databases to proprietary code and internal communications, everything is at risk in a cyberattack.
A SOC provides continuous visibility across your entire digital infrastructure. It detects unauthorized access attempts, monitors user activity, and identifies suspicious behavior before it leads to a breach. Whether you’re protecting an on-premise server, a cloud-based platform, or a hybrid environment, the SOC acts like a digital shield, proactively defending your assets from internal and external threats.
This level of protection is especially crucial for businesses that handle sensitive data or operate in regulated industries, where breaches can result in legal penalties, reputational damage, and customer churn.
24/7 Threat Monitoring and Early Detection
Cyberattacks don’t clock out at 5 PM. They can strike at any moment – overnight, during holidays, or when your internal IT team is off-duty. That’s why 24/7 security monitoring is essential.
A fully operational SOC works around the clock, scanning for real-time threats and anomalies across networks, endpoints, cloud environments, and more. By using advanced tools like SIEM, behavioral analytics, and threat intelligence, the SOC can detect even subtle indicators of compromise before they escalate into full-blown incidents.
This constant vigilance means you’re never caught off guard. You gain peace of mind knowing that someone (or rather, a whole expert team) is always watching your environment and ready to take action the moment something suspicious happens.
Minimized Damage and Faster Incident Response
The longer a cyber threat goes undetected, the more damage it can cause. Delays in identifying and containing attacks can result in prolonged downtime, data loss, and even business interruption.
A SOC is built for speed and coordination. When a threat is detected, analysts spring into action – isolating affected systems, containing the breach, and initiating remediation protocols. Well-defined incident response plans ensure that everyone knows what to do and when, turning chaos into control.
As a result, the SOC will reduce impact, enable faster recovery, and help lead to a significantly lower risk of repeat incidents. Over time, this also builds organizational resilience and sharpens your overall security posture.

Whether you’re building an SOC from scratch or optimizing an existing one, the following best practices are critical to ensure long-term success.
5. Best Practices for Building a Security Operations Center
Building a Security Operations Center is about designing a strategic foundation that aligns with your business needs and evolves with emerging cyber threats. Whether you’re building an SOC from scratch or optimizing an existing one, the following best practices are critical to ensure long-term success.
Define Your Security Needs and the Scope of Your SOC
Before you start building, you need clarity on why you need a SOC in the first place. This begins with a detailed assessment of your organization’s risk profile, regulatory environment, operational structure, and digital footprint.
You should ask questions like:
- What assets and data need the highest level of protection?
- Which systems, networks, and endpoints fall under SOC monitoring?
- What are your compliance obligations (e.g., ISO 27001, PCI DSS, GDPR)?
- How many security events does your team currently handle, and how quickly?
Defining the scope helps avoid unnecessary complexity and ensures that your SOC is right-sized, not underbuilt or overengineered. It also sets the foundation for prioritizing tools, personnel, and processes.
A clear scope also ensures executive alignment and resource commitment from the beginning, helping the SOC to integrate smoothly with business operations.
Choose the Right SOC Model: In-House, Managed, or Hybrid
Not every organization needs to build a full in-house SOC, and for many, it’s not even the most efficient or cost-effective option. Here’s a breakdown of the three main SOC models:
| SOC Model | Description | Best For |
| In-House SOC | Built and operated entirely within your organization. Offers full control. | Enterprises with large IT/security teams, high compliance needs, or sensitive data. |
| Managed SOC (SOC-as-a-Service) | Outsourced to a third-party provider that delivers 24/7 monitoring and incident response. | SMEs, startups, or organizations lacking internal security expertise. |
| Hybrid SOC | A blend of internal resources and external support (e.g., managed detection + internal oversight). | Growing companies needing flexibility or those transitioning to a full in-house model. |
Choosing the right model depends on your budget, internal capabilities, compliance requirements, and strategic goals. A hybrid SOC is often the ideal starting point as it offers scalability, cost control, and faster time to value while letting you retain visibility and governance.
In today’s world, where businesses rely more than ever on technology to operate and grow, choosing the right SOC model isn’t just a technical decision — it’s a strategic one. For many companies, especially startups or fast-growing organizations, Managed IT Services offer more than just peace of mind when it comes to security. They provide flexibility, scalability, and access to top-tier tech experts without the complexity of building everything in-house. I’ve seen organizations transform dramatically within just a few months of adopting this model — not only did they strengthen their cybersecurity posture, but they also refocused their energy on what truly matters: innovation and growth.
Integrate AI and Automation into SOC Management
Modern SOCs face thousands of alerts daily, and many of them are false positives. Without automation and artificial intelligence (AI), analysts quickly become overwhelmed, and real threats may be missed. By integrating AI and automation, SOCs can:
- Reduce Alert Fatigue: AI-driven correlation engines group related alerts, filter out noise, and prioritize critical events.
- Accelerate Response Time: Automated playbooks enable rapid response actions (e.g., isolating an endpoint or disabling a user account) without waiting for human intervention.
- Enhance Threat Detection: Machine learning models analyze behavior patterns to spot zero-day attacks or insider threats that traditional rules-based systems might overlook.
- Improve Efficiency: Routine tasks like log collection, event enrichment, and report generation can be fully automated, allowing analysts to focus on strategic investigations.
Investing in intelligent automation helps amplify the impact of your human team. It ensures your SOC can scale without requiring a proportional increase in headcount, and it future-proofs your security operations in the face of growing threat volumes.
6. Security Operations Center Solutions Built for Real-World Protection
When it comes to cybersecurity, many businesses struggle with piecing together the right tools, people, and processes. That’s where NTQ Europe comes in, delivering Security Operations Center solutions that are practical, cost-effective, and built for how businesses operate today.
Here’s what makes our approach different:
Full-Service SOC Support Tailored to Your Business
Every organization is unique, and so is its security posture. Instead of generic packages, our SOC solutions are tailored from the ground up. Whether you’re a startup looking for 24/7 monitoring or an established enterprise building an internal security hub, we help define your SOC scope, deploy the right tools, and manage day-to-day operations.
This isn’t just about keeping hackers out. It’s about building a living system that grows with your company, monitoring threats, reacting in real-time, and continually improving based on real data.
Smart Integration of the Right Tools
An effective SOC is staffed with good people and also powered by the right technology. We bring together key components like:
- SIEM platforms that centralize data and highlight threats before they escalate.
- Threat intelligence feeds that keep your team one step ahead of attackers.
- Automation and AI that reduce manual work, filter noise, and respond instantly to critical events.
This smart ecosystem ensures you’re not drowning in alerts. Indeed, you’re working with insight, speed, and precision.
Built to Perform, Without Breaking Your Budget
Security doesn’t need to be expensive to be effective. Our SOC consulting focuses on what matters most: defining a security model that fits your budget, matches your growth stage, and meets industry compliance standards.
We help you choose between in-house, managed, or hybrid SOC models and guide you on deploying the tools and teams that give you the most protection for your investment. And because we work globally, we understand how to build SOCs that balance quality with efficiency.
7. A Strategic Investment in Cyber Resilience
A well-structured Security Operations Center is now a strategic necessity in this digital landscape to protect your business from cyber threats, empowering businesses to proactively defend against security risks, detect threats in real time, and respond with confidence before damage is done.
Investing in a SOC will help protect your sensitive data while strengthening your organization’s operational resilience, building customer trust, and ensuring long-term business continuity.
Whether you’re a startup, SME, or large enterprise, NTQ Europe offers advanced, scalable SOC solutions tailored to your industry and needs. We combine cutting-edge technology, global expertise, and personalized guidance to help you build a safer, smarter digital future.
Ready to take control of your cybersecurity? Contact us today to build a Security Operations Center that protects your business 24/7 without compromise.