1. The Pain of Firmware Updates in Industrial IoT Is Real
Why Industrial Environments Are Inherently Unstable
Factory floors, remote sites, and field-deployed devices rarely offer the luxury of stable internet or uninterrupted power. Devices might sleep for hours to save energy or rely on spotty Wi-Fi or Zigbee mesh networks. In these environments, even transferring a small firmware package can be risky.

What Happens When Updates Go Wrong
Failed updates aren’t just annoying—they can brick entire fleets of devices, disrupt operations, or expose equipment to vulnerabilities. Sometimes, there may be no easy way to recover the device remotely. Worse yet, a botched update in a critical system could risk operator safety or compliance.
The Hidden Costs of Manual or Reactive Firmware Management
When companies lack a reliable OTA firmware update for industrial IoT strategy, they often rely on field visits, USB flashes, or risky SSH access. That means more downtime, labor hours, and longer lead times to fix simple issues. All of it adds up, quietly draining efficiency and budget.
2. What Makes OTA Firmware Update So Challenging in Industrial Settings
Connectivity Gaps and Low-Power Constraints
Unlike consumer devices, industrial IoT nodes often sleep most of the time to conserve energy. Many are battery-powered or run on energy harvesting, making always-on connectivity unrealistic. Updates must be scheduled intelligently, buffered securely, and resumed if interrupted.
Firmware Security, Version Drift, and Integrity Checks
Security is central to a reliable update process. Each firmware package should be encrypted, digitally signed, and thoroughly validated before and after installation. Devices also need a rollback mechanism if something breaks during reboot. As more devices come online and updates get staggered, maintaining consistent firmware versions becomes a challenge that can’t be ignored.

Managing Hundreds (or Thousands) of Devices Remotely
As fleets grow, even simple tasks become complex. Different hardware versions, varying network conditions, and patch prioritization create a coordination nightmare. You need a system that handles scheduling, targeting, retry policies, and update confirmation—all with minimal human intervention.
3. What a Good OTA Firmware Update Strategy Should Look Like
Secure Delivery with Fail-Safe Mechanisms
A resilient system encrypts firmware at rest and in transit, validates signatures, and stores a known-good fallback in case of failure. Devices should be able to detect failed boots and automatically restore the previous version.
Lightweight Protocols for Low-bandwidth Networks
HTTP and MQTT are popular because they work over poor connections. But protocol choice matters. Custom approaches (like multicast updates or staggered delivery) might be needed for mesh networks or very low-power nodes.
Real-Time Monitoring, Scheduling, and Rollback Logic
A solid OTA setup should show you what’s happening live. You’ll want to see which devices are done, which are stuck, and which need help. Smart systems let you schedule rollouts when they are quiet and stop them quickly if something breaks. When things go wrong, fast rollback keeps problems from spreading.
4. A Practical Roadmap for OTA Firmware Update in Industrial IoT
Step 1: Audit Your Firmware & Device Fleet
Get a clear view of what’s out there: device types, firmware versions, and hardware limits. Knowing this upfront helps you avoid surprises mid-update.
Step 2: Define Update Triggers, Rollback, and Alert Rules
Set clear rules for when updates should happen (e.g., on reboot, on schedule, on manual trigger). Define thresholds for retry attempts, alert escalation, and failure handling.
Step 3: Choose Infrastructure – Cloud, Edge, or Hybrid
Depending on latency and data privacy needs, you may run the OTA engine in the cloud, on-premises, or on a local edge gateway that syncs with your core systems.
Step 4: Build, Pilot, Iterate, Scale
It’s better to begin with a focused pilot—one site, one fleet segment—where you can validate performance, observe edge cases, and fine-tune rollout logic. These early insights help you scale more confidently without exposing your entire system to risk.
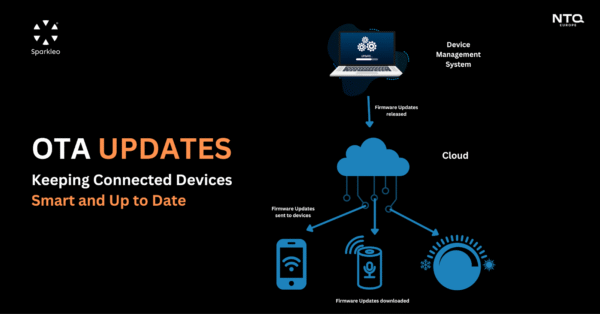
5. Where NTQ Europe Comes In
From Embedded to Cloud: A Unified OTA Framework
NTQ Europe designs OTA-ready firmware architectures from day one—combining embedded, mobile, and cloud expertise. Whether you’re deploying ESP32, STM32, or custom SoCs, we build in update logic that survives real-world conditions.
Experience with ESP32, Zigbee, Custom Firmware Pipelines
We’ve built and deployed OTA systems over Zigbee mesh, Wi-Fi, and cellular for use cases in asset tracking, smart factory devices, and predictive maintenance. Our clients rely on us to simplify a complex and fragmented process.
Helping Clients Scale OTA Securely Across Fleets
With centralized dashboards, alerting, and version tracking, we help clients scale confidently from pilot to production without service disruption.